Do you comply with the Essential Eight?
Don’t wonder if, let us help you find out and get your business secure. The Pro Computers team can help you understand, implement, and assist you with managing the Essential Eight Strategies in your business. Contact Pro Computers today for a no-obligation, Free onsite discussion to help you get started.
Have you heard of the Essential Eight?
If you haven’t, your current IT provider may not be providing you with total Cyber Security Services.
What are the Essential Eight?
The Essential Eight are the recommended cyber strategies for businesses by the Australian government.
Below is a short translation of the Essential Eight from Tech language to Lay terms.
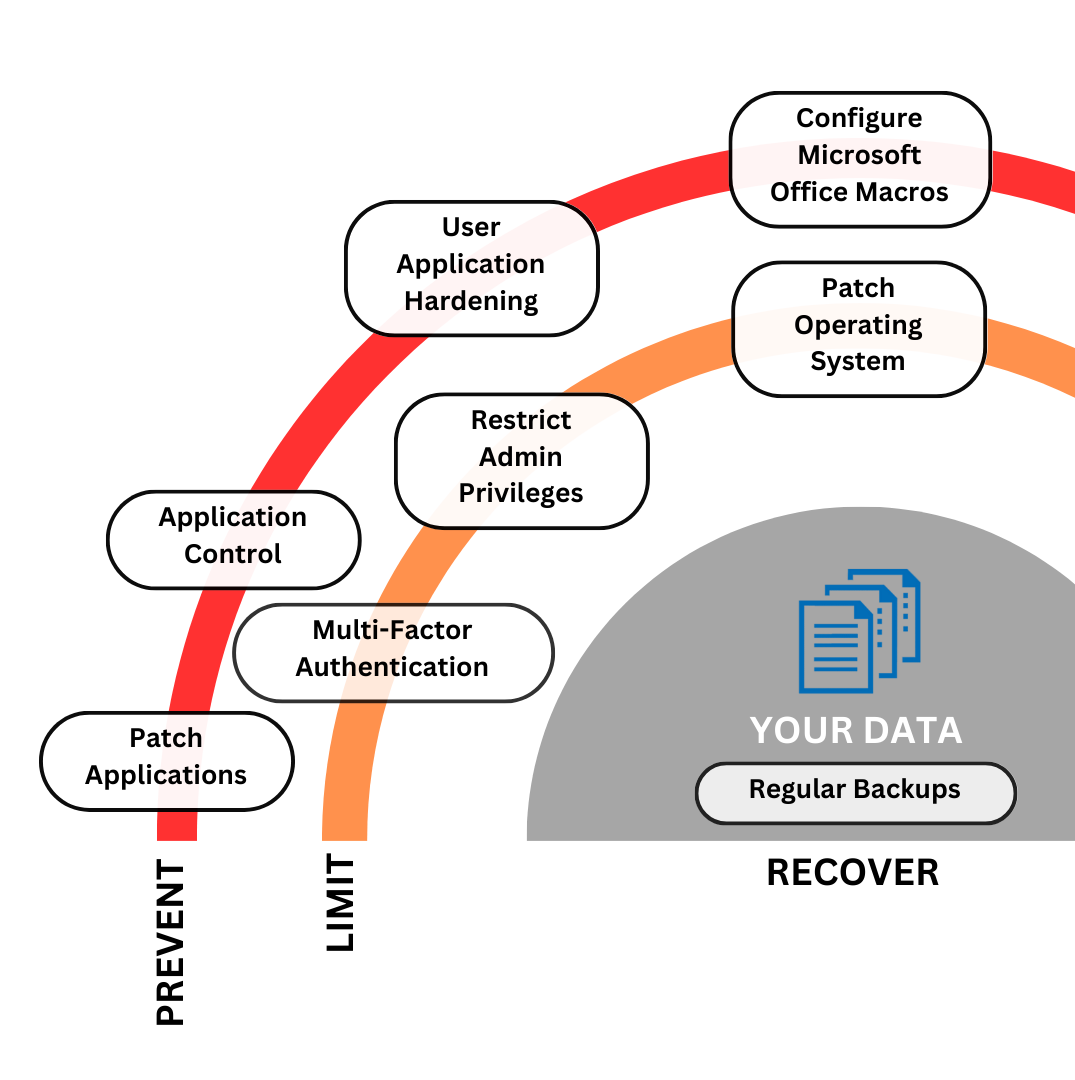
The mitigation strategies that constitute the Essential Eight are:
1. application control
Restrict applications to decrease the risk of cyber hacks to your business data.
2. patch applications
To fix known issues or fault in your software.
3. configure Microsoft Office macro settings
Remove the risk of accidental or unwanted access to sensitive content.
4. user application hardening
Lower the risk from required applications being exploited.
5. restrict administrative privileges
Prevent accidental damage to your network from unapproved applications or setting changes.
6. patch operating systems
Lower the risk of a vulnerability being exploited causing exposure or damage to your data and systems.
7. multi-factor authentication
An added security layer to access your data, applications or systems.
8. regular backups
The ability to recover before a cyber event occured.
**More information can be found here >> https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/essential-eight/essential-eight-explained



